
What is Polkit?
A memory corruption vulnerability was discovered in pkexec of polkit (previously PolicyKit).
Polkit is a SUID-root program that is installed by default on every major Linux distribution. The vulnerability (CVE-2021-4034) was discovered by the Qualys Research Team.
It can be easily exploited to gain root access to an unprivileged user by exploiting it in its default configuration.
Bharat Jogi, Director of Vulnerability and Threat Research at Qualys stated that PwnKit is “a memory corruption vulnerability in Polkit, which allows any unprivileged user to gain full root privileges on a vulnerable system using default polkit configuration.”
And as a fact, the vulnerability had been there (hiding in plain sight) since the first version of pkexec in May 2009, affecting all the versions.
Impact of PwnKit (CVE-2021-4034) vulnerability
The pkexec could be used to gain root access in the vulnerable system by any of the unprivileged users. Less than three hours after the technical details were published, the exploit to the same emerged in the public spaces.
The security research team at Beagle Security successfully compiled and tested the available exploit, by which we could gain root access to the vulnerable systems from an unprivileged user’s account.
And it was found to be vulnerable on default installations of Linux distros such as Ubuntu, Fedora, Debian, and CentOS.
This could also mean that other Linux distributions are also likely to be vulnerable and exploitable since pkexec has been vulnerable for over 12+ years.
The POC of our findings is given below.
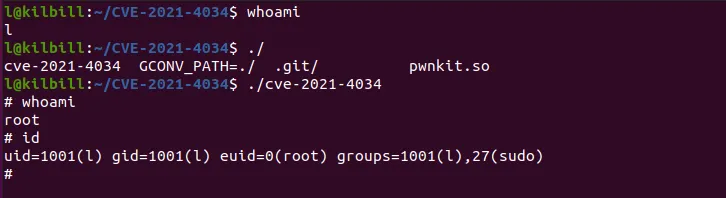
And according to statements by CERT/CC vulnerability analyst Will Dorman, ARM64 architecture was also found to be vulnerable by the same. He also said that this exploit is “simple and universal.”
How to fix PwnKit (CVE-2021-4034) vulnerability
Security updates have already been pushed by some of the Linux distros. Ubuntu has already pushed updates for PolicyKit for the same in versions 14.04 and 16.04 as extended security maintenance (ESM). The users only need to have a normal system update and then perform a system reboot on the machines for the security patch to take effect.
However, the temporary mitigation for operating systems that had not yet published the security patch would be to use the change mode command (chmod) to strip pkexec of the setuid bit as shown below.
chmod 0755 /usr/bin/pkexec





