
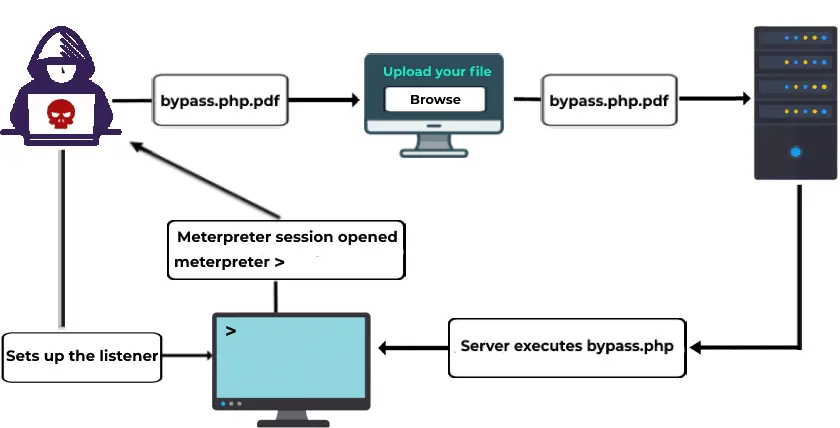
File upload vulnerability is a common security issue found in web applications. Whenever the web server accepts a file without validating it or keeping any restriction, it is considered as an unrestricted file upload.
In many web servers, the vulnerability depends entirely on its purpose, allowing a remote attacker to upload a file with malicious content. This might end up in the execution of unrestricted code in the server. File upload vulnerability can be exploited in many ways, including the usage of specially crafted multipart form-data POST requests with particular filename or mime type.
The consequences include whole system acquisition, an overloaded file system or database, diverting attacks to backend systems, and simple defamation.
Types of file upload vulnerability
Local File Upload Vulnerability
Local file upload vulnerability allows an application user to upload or drop a malicious file directly into the website.
Given below is an example program that allows an attacker to upload a malicious file to an application:
<?php
$target_dir = "uploads/"; //specifies the directory where the file is going to be placed
$target_file = $target_dir.basename($_FILES["fileToUpload"]["name"]);
//specifies the path of the file to be uploaded
$imageFileType = strtolower(pathinfo($target_file,PATHINFO_EXTENSION)); //holds the file extension of the file
Given below is the code that shows that this vulnerability can be avoided by verifying the user license:
if (!current_user_can('upload_files')) //verify current user has the permission to upload a file
die(__('You do not have permission to upload files.'));
// Process file upload
This protection can be bypassed with some extensions (eg: double extensions) that are executable on the server but not listed. (Example files: “file.php5”, “file.shtml”,”wecome.html.fr”,“file.asa”, or “file.cer”)
Remote File Upload Vulnerability
When an application does not allow its users to upload a file directly and instead provides a permission to give a URL, then remote file upload vulnerability is possible. The user uploaded file is then saved into the disk in a publicly accessible directory.
After that an attacker can execute the file and gain access to the website. Once an attacker has gained access, they can compromise the restricted data or even perform denial of service attacks.
The “Tim thumb vulnerability” that has affected a huge number of plugins was a remote file upload vulnerability. In this case, the image library allowed developers a way to specify an image URL in the query string.
So, TimThumb.php will download that image from the web. Attackers can manipulate the image URL and create a php file that is hosted on their website. Then Tim thumb will store the php file in the victim’s website which can be publicly accessible. This paved the way for attackers to access the php file and execute malicious scripts.
Impact of file upload vulnerability
Takeover of the victim’s entire system through a server-side attack.
Files are injected through the malicious paths. So, existing critical files can be overwritten as the .htaccess file can be embedded to run specific scripts.
Inject phishing pages to discredit the web application.
File uploads may expose critical internal information in error messages such as server-internal paths.
How to prevent file upload vulnerability
A file upload vulnerability can be prevented by following the below mitigation techniques:
Allow only certain file extension
Set maximum file size and name length
Allow only authorized users
Make sure the fetched file from the web is an expected one
Keep your website updated
Name the files randomly or use a hash instead of user input
Block uploads from bots and scripts using captcha
Never display the path of the uploaded file





