
EXIF stands for Exchangeable Image File Format and the EXIF data contains information such as the camera model and make, shutter speed, aperture, focal length, ISO number, date, time and much more. It can also store GPS coordinates of the location where an image was shot.
While being able to read such data is good to find out what settings were used to create a particular photograph, understanding photo metadata and how it can work against you is also important.
Even if you are not concerned about privacy, you would never want someone to get hold of sensitive personal information.
Many social media platforms remove the metadata from the images but there are still many images online where this information is available and can be easily extracted.
The following image shows an example of the photo metadata.
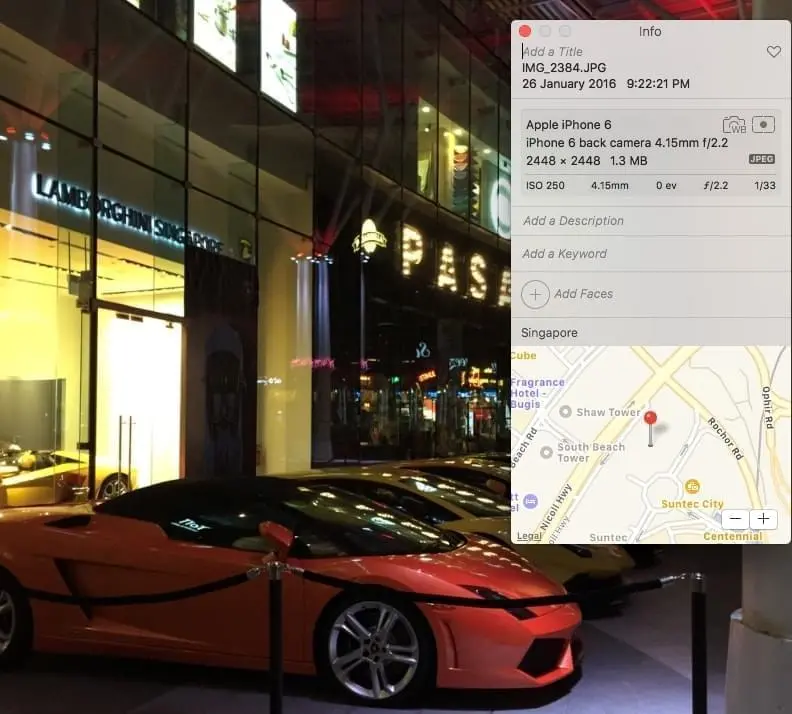
You can see that it contains information like the device used, focal length, aperture, ISO number, shutter speed and most importantly the exact geolocation data of where the image was taken.
Impact of Information Leakage in Image EXIF Data
This data breach is critical due to the following reasons:
An attacker can get the exact location where a particular photo was taken
A photo can be easily replicated by using the metadata of the image
The following image/picture shows an example of the data stored in the image metadata.
How to Prevent Information Leakage in Image EXIF Data
We recommend the following measures to avoid exposing sensitive information in image metadata:
Disable geotagging on the digital device you use to take photographs
Use an image processing software or EXIF data remover tool to delete metadata





