
What is DNS zone transfer?
DNS zone transfer, also known as DNS query type AXFR, is a process by which a DNS server passes a copy of part of its database to another DNS server. The portion of the database that is replicated is known as a zone.
A zone transfer uses the Transmission Control Protocol (TCP) and takes the form of a client-server transaction.
The client requesting a zone transfer may be a slave server or secondary server, requesting data from a master server or a primary server.
When does a DNS zone transfer usually occur?
A zone transfer usually occurs when you bring up a new DNS server as a secondary DNS server.
A full transfer of all the zone information will take place in order to replicate the already existing records for that zone. This a time-consuming and resource-intensive process. Thus, incremental DNS transfers were developed.
In the Incremental Transfer, the server retrieves only the resource records that have changed within a zone so that it remains synchronized with the primary DNS server.
When using incremental transfer the SOA record is compared to see whether any changes have been made. If the primary name server has a higher SOA version number than the secondary name server then a zone transfer will be initiated.
If the SOA records version number is the same, a zone transfer will not be initiated.
When changes have been made to the zone file on the primary name server and there is a DNS notify list, the primary name server immediately notifies the secondary name server that the zone file has been modified. It then instructs it to initiate a zone transfer without waiting for the refresh interval to expire.
The notify list is a list of IP addresses that specify which secondary name servers are allowed to access zone information on the primary name server for purposes of zone transfer.
Here is an example showing how to perform a DNS zone transfer using dig:
Command:
dig axfr @nsztm1.digi.ninja zonetransfer.me
Here, nsztm1.digi.ninja is the nameserver and zonetransfer.me is the domain name.
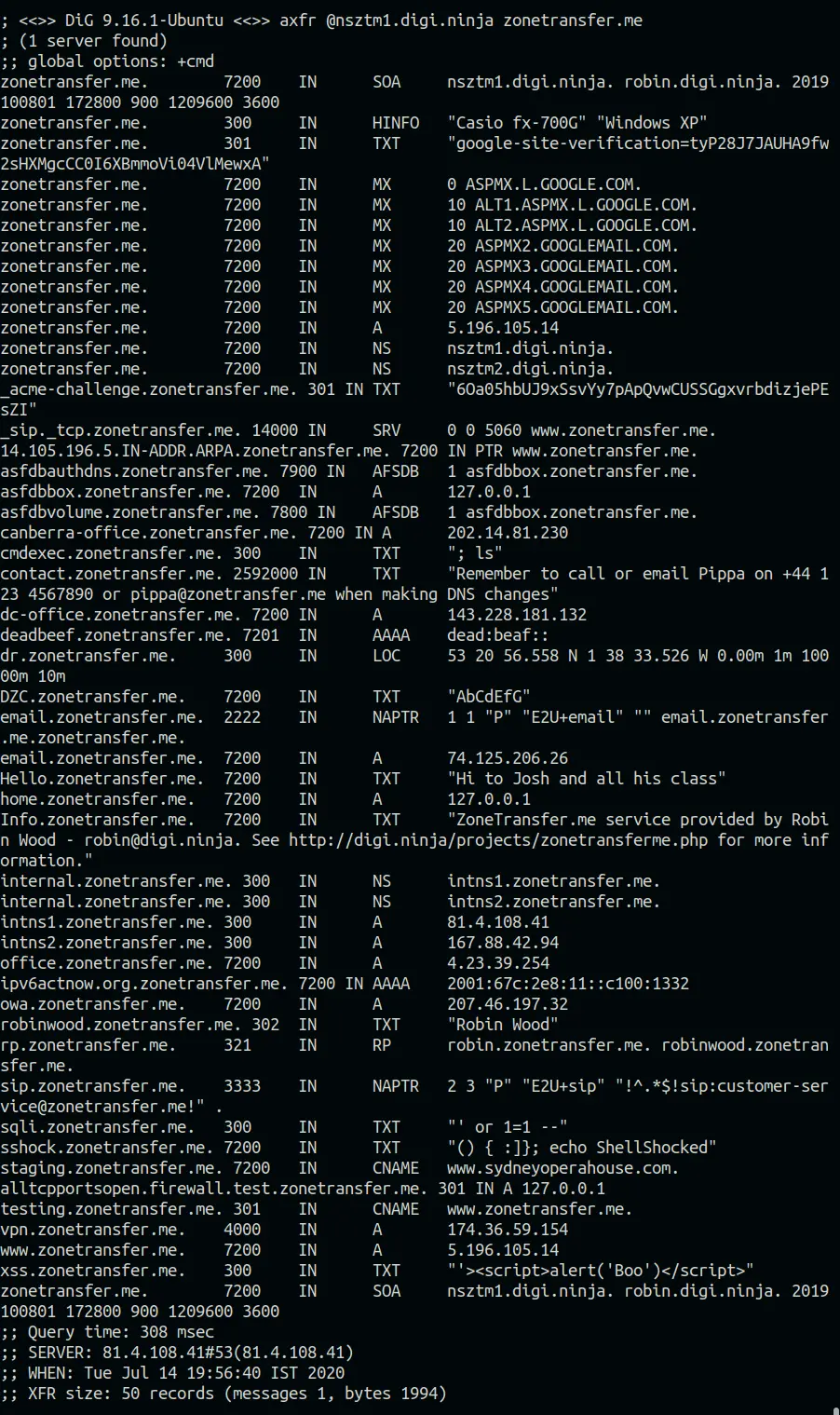
These DNS records are further explained below.
SOA record
Information stored in a DNS zone starts with an SOA (Start Of Authority) record.
This record contains information about:
the name of the server
name of the administrator of the zone
the current version of the SOA record
the number of seconds a secondary nameserver should wait before checking for any updates
the number of seconds to wait before retrying a failed zone transfer
the maximum number of seconds that a secondary nameserver can use data before it must either be refreshed or expire
the default number of seconds for the time-to-live (TTL) file on resource records.
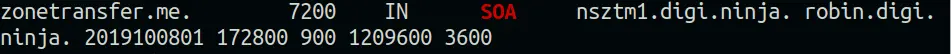
Here:
zonetransfer.me is the name of domain
nsztm1.digi.ninja.is the primary name server
robin.digi.ninja. represents the person in charge of the domain
the email address (swap first . for an @)
2014101601- The current SOA serial number for the domain
172800- number of seconds that a secondary name server should wait between making requests for changes
900- Number of seconds a primary name server should wait if it fails to refresh properly
1209600- Number of seconds that a secondary name server can claim to have authoritative information
3600- Minimum TTL
MX record
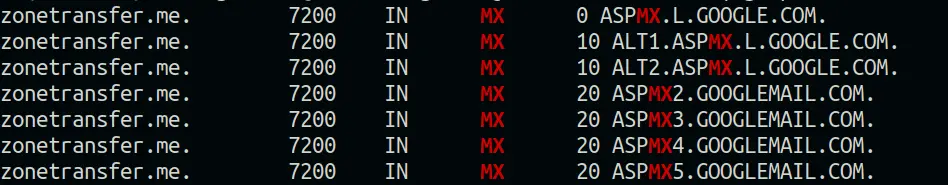
A Mail eXchange record (MX record) specifies the mail server responsible for accepting email messages on behalf of a domain name. Here the victim uses Google’s mail service. This is useful information when performing any social engineering attacks.
TXT record
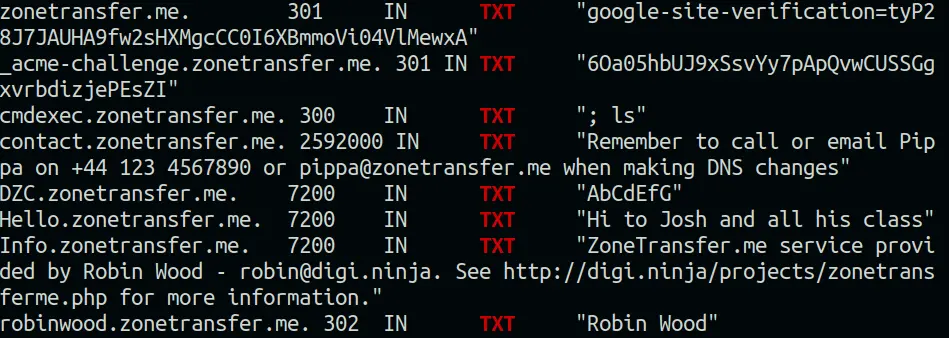
A Text (TXT) record is a type of resource record in the Domain Name System (DNS) used to provide the ability to associate arbitrary text with a host or names, such as human-readable information, network, data center, or other accounting information.
TXT records may contain valuable information. From this TXT record, we obtained an email id and a phone number.
SRV record
A SRV (Service) record shows the location of the SIP server, identifies a service by showing the protocol, host, and port it is running on.

This points to a server named _sip._tcp.zonetransfer.me listening on TCP port 5060 for Session Initiation Protocol (SIP) and www.zonetransfer.me is the host providing the service. The priority given here is 0, and the weight is 0.
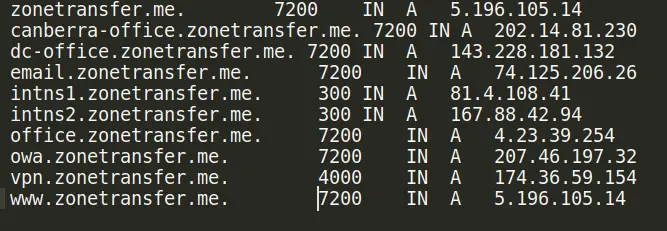
A record
A record maps a domain name to its corresponding IP address. From A record we got three data center IPs and three office IPs which gives a total of 6 targets.
CNAME
A Canonical Name (CNAME) record is used to map an alias from one domain name to another domain name. From this, we can see a testing and staging server.

Impact of DNS Zone Transfer Vulnerability
DNS zone transfer offers no authentication. So, any client or someone posing as a client can ask a DNS server for a copy of the entire zone.
This means that unless some kind of protection is introduced, anyone is capable of getting a list of all hosts for the particular domain, which gives them a lot of potential attack vectors.
How to Prevent DNS Zone Transfer Vulnerability?
- Only allow a zone transfer from trusted IPs. The following is an example of how to fix this in the BIND DNS server.
Navigate to /etc/named.conf and add these:
ACL trusted-servers
{
173.88.21.10; // ns1
184.144.221.82; // ns2
};
zone securitytrails.com
{
type master; file "zones/zonetransfer.me";
allow-transfer { trusted-servers; };
};
- Use Transaction SIGnatures (TSIG) for zone transfers





