
Two remote command execution vulnerabilities in the Java Spring framework were made public in late March 2022.
The first of these flaws affects a framework component known as “Spring Cloud Functions.” The second, and arguably more serious vulnerability affects a component in “Spring Core,” the framework’s heart, significantly increasing the vulnerability’s potential impact and earning it the moniker “Spring4Shell”.
CVE-2022-22965 (Spring4Shell) is a Spring Framework vulnerability that uses data binding functionality to bind data stored in an HTTP request to specific objects used by an application.
The flaw is in the getCachedIntrospectionResults method, which can be used to gain unauthorized access to such objects bypassing their class names through an HTTP request.
When special object classes are used, it introduces the risk of data leakage and remote code execution.
Fortunately, despite the widespread use of the Spring Framework, the conditions under which the vulnerability can be exploited are relatively limited.
A vulnerable configuration consists of:
JDK version 9+
Spring Framework versions 5.3.0 to 5.3.17 and 5.2.0 to 5.2.19 and below
Apache Tomcat as the servlet container
Packaging as a traditional WAR (in contrast to a Spring Boot executable jar)
Usage of the
spring-webmvcorspring-webfluxdependency
How to address the Spring4Shell vulnerability
Upgrading to Spring Framework to 5.3.18 and 5.2.20 is the most effective way to address the Spring4Shell vulnerability.
You can upgrade Maven by adding the following entry to your POM file:
<spring-framework.version> properties
5.3.18
</spring-framework.version>\s</properties>
Add the following to Gradle:
spring-framework.version = '5.3.18'
There are a few workarounds you can use if you are unable to upgrade the Spring Framework. These are the options:
Downgrade JDK to version 8.
Tomcat should be upgraded to 10.0.20, 9.0.62, or 8.5.78.
Implement blocklists within the application to prevent vulnerable functionality from being called. More information and examples can be found in the Spring Framework blog post,here.
How Beagle Security helps you mitigate Spring4Shell
Beagle Security can detect Spring4Shell vulnerabilities through real-time exploitation and reporting, allowing customers to mitigate them.
Although internal checks are already available on every test, we recommend that you schedule a security test to review the security of your systems.
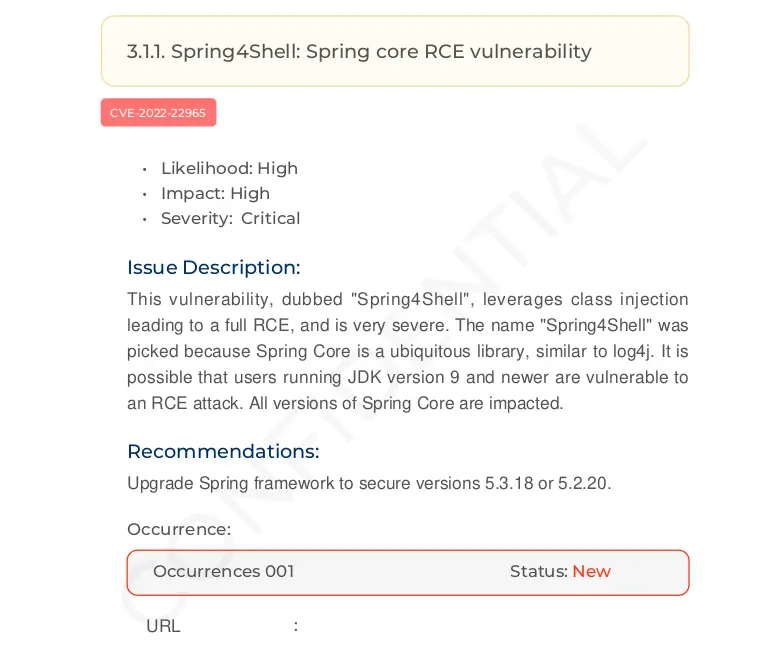
A screenshot of the Beagle security report page displaying the discovered Spring4Shell Command Injection vulnerability.

