The Context
In today’s digital world, web application security plays an important role in the overall cyber security of an organization. Usually different teams in the organization are not aware about the various application threats that can finally compromise assets of the organization. So in order to counter various cyber risks the most important decision you can take is to educate yourself and the team about the threats, its impact and its likelihood. Threat modeling is an activity that will help to create a security profile for each application so that the team can understand hidden threats and its risks.
When should you start modeling the threats?
Creating a secure web application is not a trivial task. To implement a secure web application the development team should have clear understanding about the assets and the threats for that assets. Threat modeling is a design and analysis technique that shall be used to identify a projects security requirements. The inclusion of threat modeling in the early development stages of an application will help to reduce the cost to fix the vulnerabilities. But that doesn’t prevent it from using on projects and solution which are already in production.
How to model threats?
The process in a nut shell is as shown below.
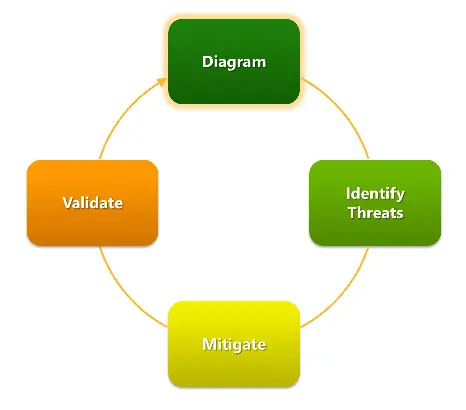
Threat modeling should be an activity involved by all the relevant stakeholders of the project, which will in turn give them a sense of ownership and understanding about the projects security requirements. An ideal team should include application architects, security professionals, developers, testers, and system administrators. There are different approaches practiced by security experts in the industry. Whatever approach you chose it involves the following 5 major steps.
| Step | Description | |
|---|---|---|
| Step 1 | Establish security objectives | Clear vision on security objectives for the project will help you to control the following steps. |
| Step 2 | Model Applications Environment | Modeling the application’s architecture and actors will help to clearly identify relevant threats. |
| Step 3 | Decompose Application and its Environment | The detailed modeling will help you to disclose the hidden threats. |
| Step 4 | Identify Threats | From the output of above two steps identify the Threats. |
| Step 5 | Identify Vulnerabilities and Mitigation | List the vulnerabilities where mistakes are often made. |
How to diagram the application models?
There are different approaches followed in the industry to diagram the application model. We at Appfabs follow the approach explained in Microsoft Security Development Lifecycle. It uses the Data Flow Diagrams and its symbols to model the Application Environment and Actors. The following screen shot shows a sample diagram in which application environment is modeled for Threat Modeling.
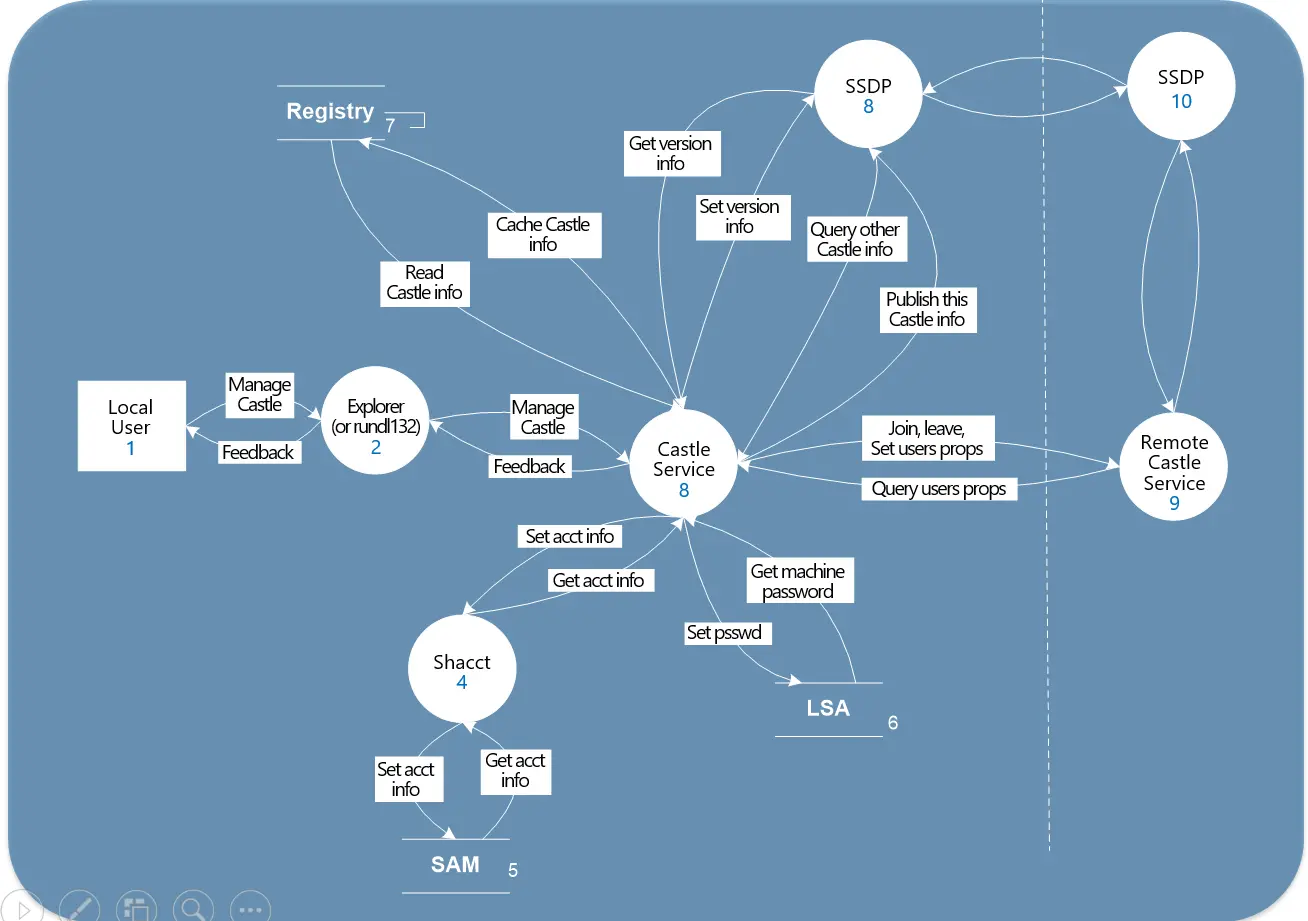
This model will serve as the baseline for identifying the important aspects of every system: The entry and exit points, the Assets, the Trust Levels and the Threats.
How to Identify Threats?
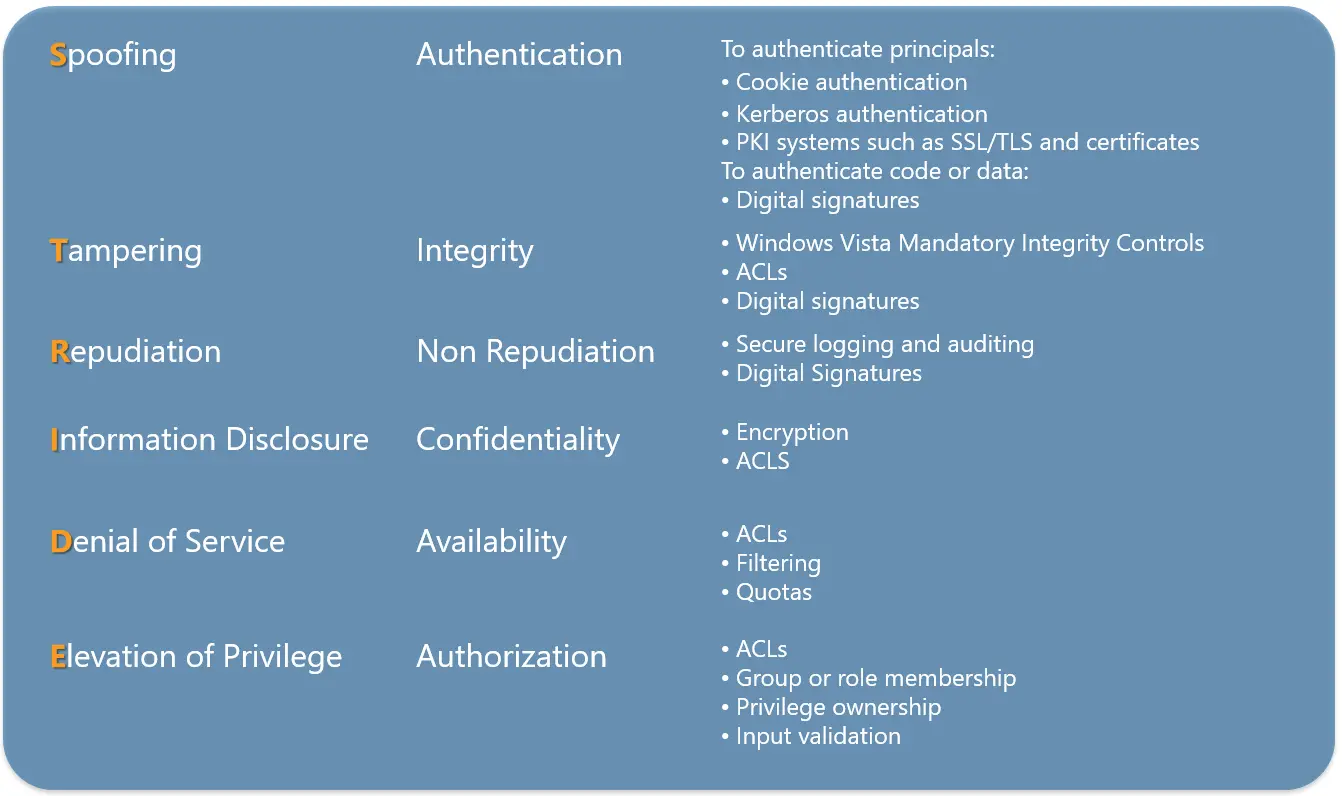
To manage the identification of Threats it will be a good idea to use a standard Threat categorization framework called STRIDE. The STRIDE threat model helps to place threats into different categories so that right questions can be formulated from the attacker’s point of view. STRIDE focuses on six common types of threats which an attacker usually consider to penetrate the system.
| Threat | Weakness which is exploited for this threat. |
|---|---|
| Spoofing | Authentication |
| Tampering | Integrity |
| Repudiation | Nonrepudiation |
| Information Disclosure | Confidentiality |
| Denial Of Service | Availability |
| Elevation of Privilege | Authorization |
So based on application model we built on the first step we will be to identify which all threats are relevant for the application for which we are modeling the threats. The following table shows the kind of threats that can effect each element in the application model.
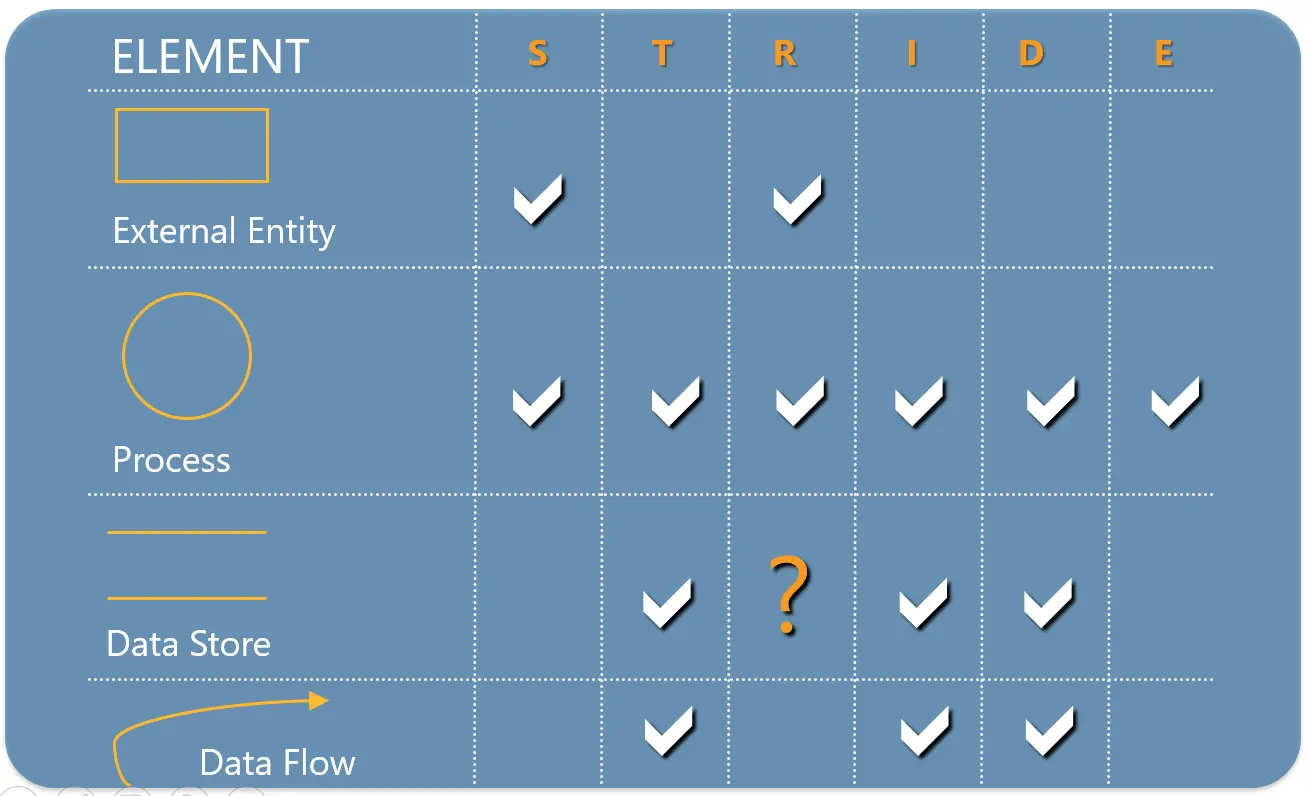
Applying STRIDE threats to each element will give a comprehensive threat landscape for the target application. This comprehensive knowledge about the threat landscape will help the team to plan, design and implement the mitigation strategies for each and every threats.
How to deal with the identified Threats?
The whole point of Threat Modeling is to address each and every relevant threat and protect the assets. So with the insight gained in the previous steps the team has to think about the mitigation steps for each threat. The following are common approaches we usually follow to address each threats.
- Redesign to eliminate
- Apply standard mitigations
- Apply the standard mitigations specified in the industry.
- Invent new mitigations (Not Recommended)
- Accept vulnerability in design.
- In cases where a security vulnerability cannot be removed, for any reason.
The following Table shows the common mitigation steps for each category of threats.
How do you ensure the identified threats are mitigated?
Threat modeling and documenting will not ensure a secure system, it only a step towards it. The team should also validate the model frequently and make changes based on the changes happening in the application and deployment scenarios and make sure the mitigations are done properly. As part of validation do ensure the following points.
- Does the diagram match the final state of the application?
- Are all threats enumerated?
- Has all stake holders reviewed the Threat Model.
- Is each threat mitigated?
- Are mitigations done right?
Conclusion
As OWASP explains its Threat Modeling motto, “The sooner the better, but never too late”. Embrace Threat Modeling in your SDLC to be proactive and strategic in your operational and Application Security.